How-To use Evil Limiter on Kali
Evil Limiter is a superb utility for analysing and limiting bandwidth used by hosts on your local network.
First a disclaimer: Everything I've performed and illustrated here was performed on my own network, with my own host devices. You should never interfere or disrupt any hosts or networks without the explicit permission of the network & host owners or operators. Doing so in most juristrictions is likely to be illegal, with the risk of associated penalties for performing any illegal activities.
Quoting directly from the Evil Limiter github page, Evil Limiter is "a tool to monitor, analyze and limit the bandwidth of devices on your local network without physical or administrative access."
It is an easy to use frontend which "employs ARP spoofing and traffic shaping to throttle the bandwidth of hosts on the network."
To install Evil Limiter, the first step is to clone the github repository:
git clone https://github.com/bitbrute/evillimiter.git
Once this is cloned, it easily installed with a few commands shown below:
cd evillimiter
sudo python3 setup.py install
After the install is completed, Evil Limiter can started from the command line:
sudo evillimiter
The Evil Limiter application starts up with some basic information about your local environment, including the gateway (default router) ip address and the local subnet mask:
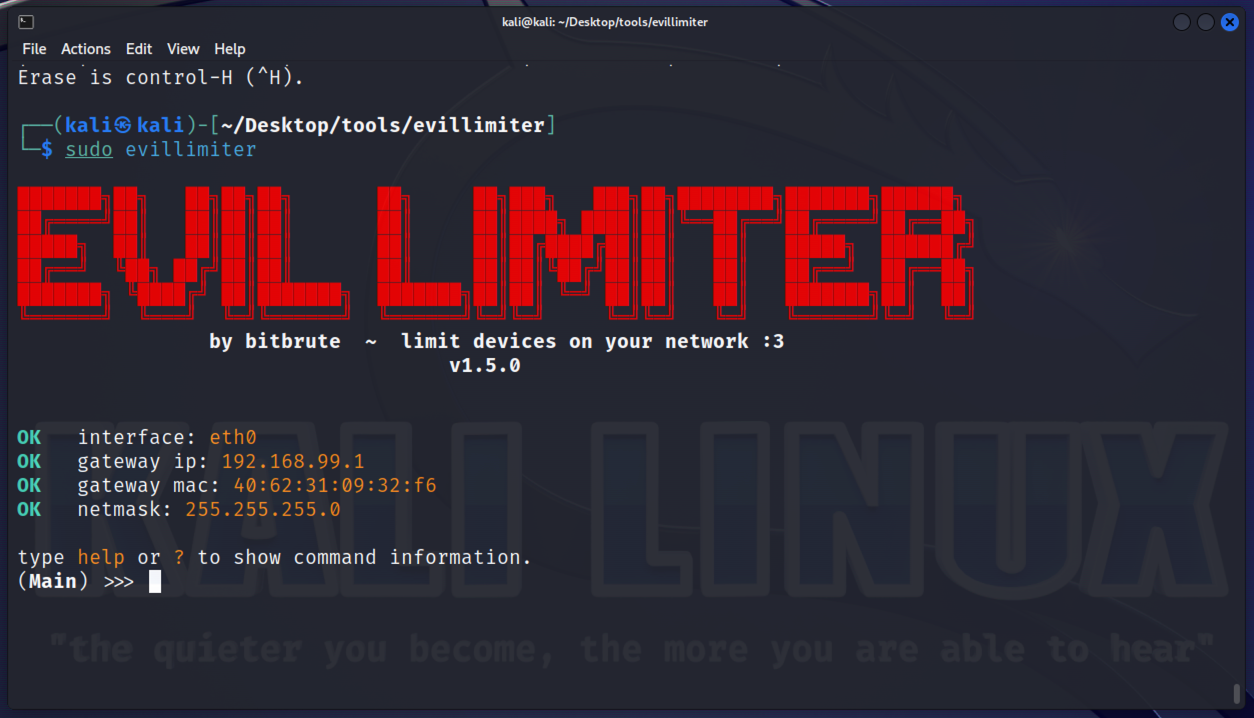
At the (Main) >>> prompt, Typing ? will present the available commands.
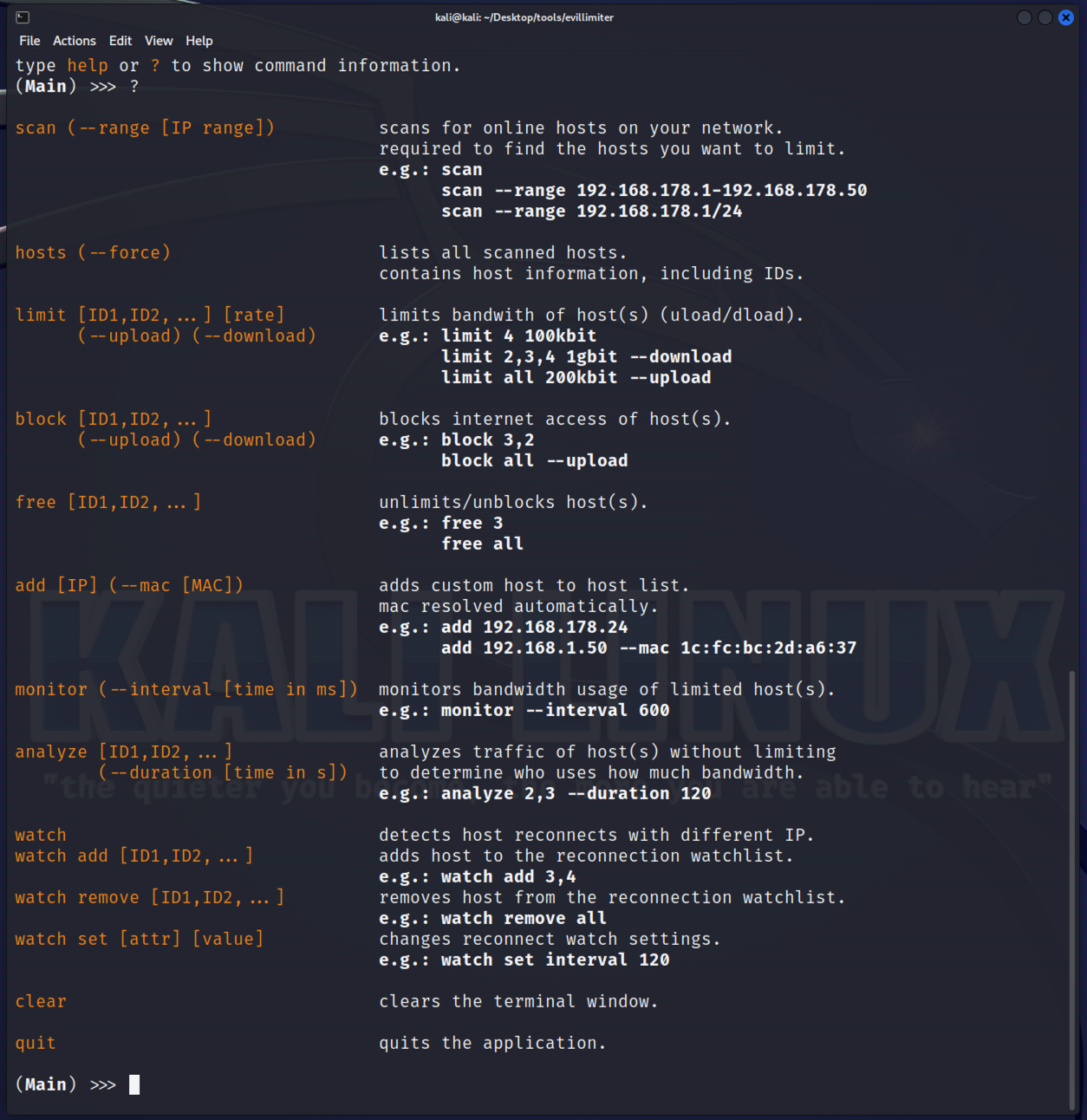
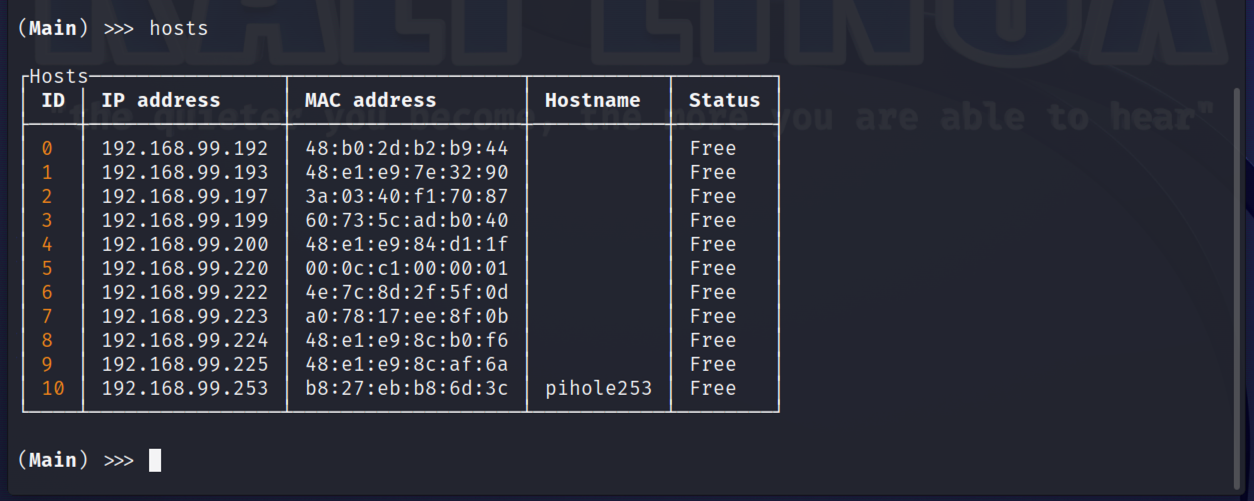
To start with, type scan with a range if you wish, otherwise the entire local subnet will be scanned for hosts. In this example, I'll just scan the upper half of my local subnet to keep the information brief. There may be the odd warning regarding Mac address not being found. We can check hosts we have discovered, and simply rescan should the appropriate target not being identified.
In my partial scan of my local subnet 11 hosts have been identified, including my PiHole. The host using the IP of 192.168.99.197 is listed under the Host ID of 2, this is my mobile phone, and will be the host I will use to demonstrate some of the Evil Limiter abilities.
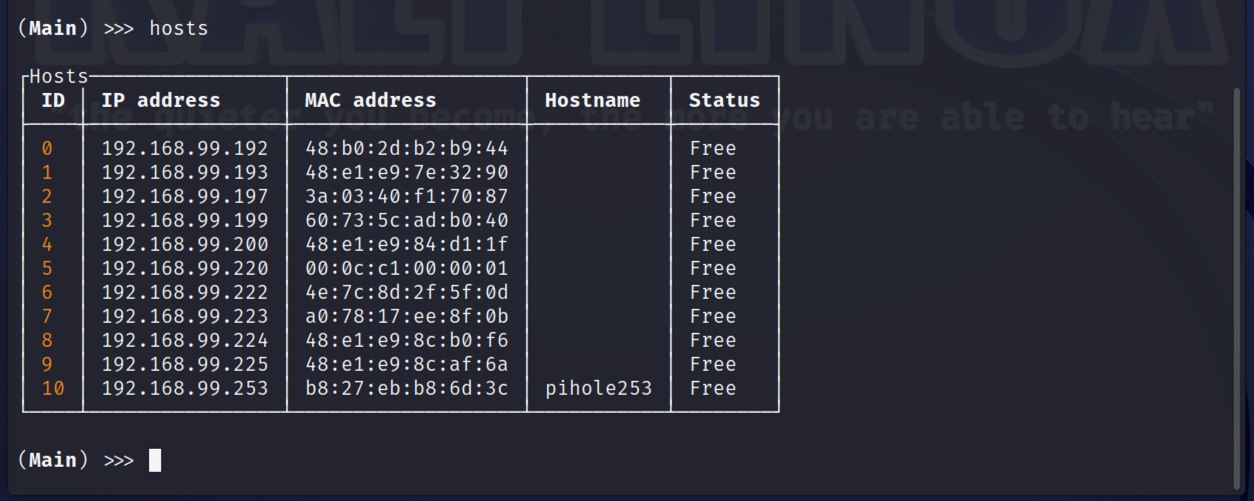
Just in case anyone is interested, I personally can't see the point of blocking out or hiding MAC Addresses or RFC-1918 IP addresses. Unless you are up to some acts that are illegal or irresponsible, worrying about your MAC Addresses is in my view a concern too far.
So moving on, we can analyze traffic for a given host to get a feel for how much data is being transfered. In the two examples below, the first was whilst a youtube video was playing, the second was whilst performing a speedtest from my phone.
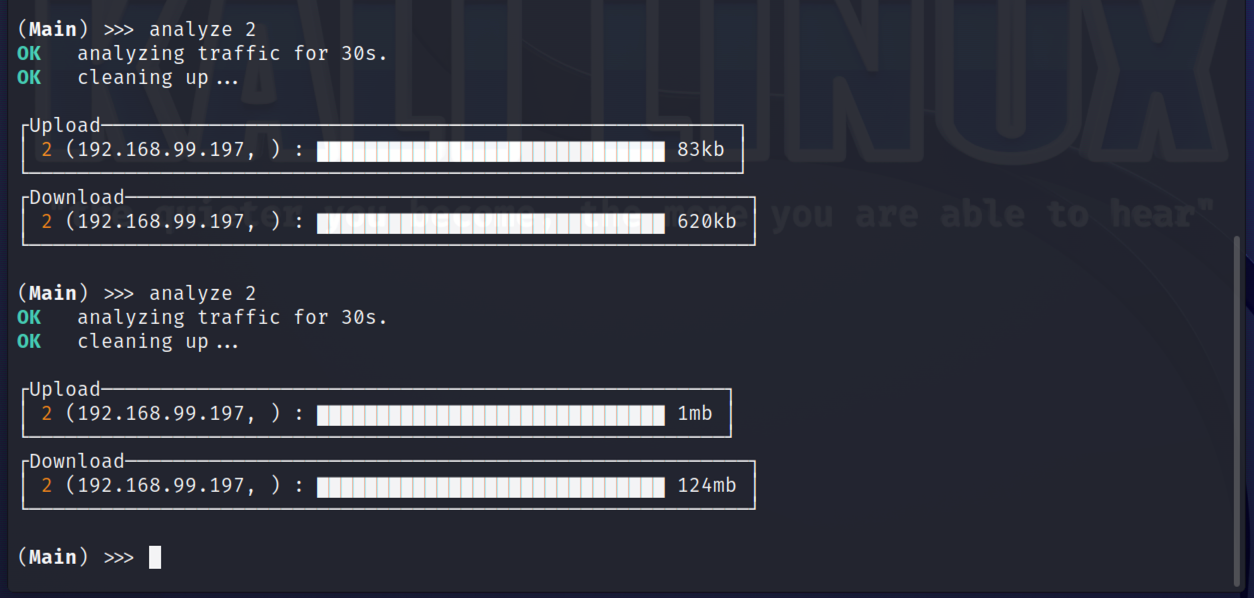
To limit traffic levels for a device, simply use the limit command along with the host ID and the limit to be applied in either kbit / mbit or gbit. Below I have limited my phone to just 25Mbps.
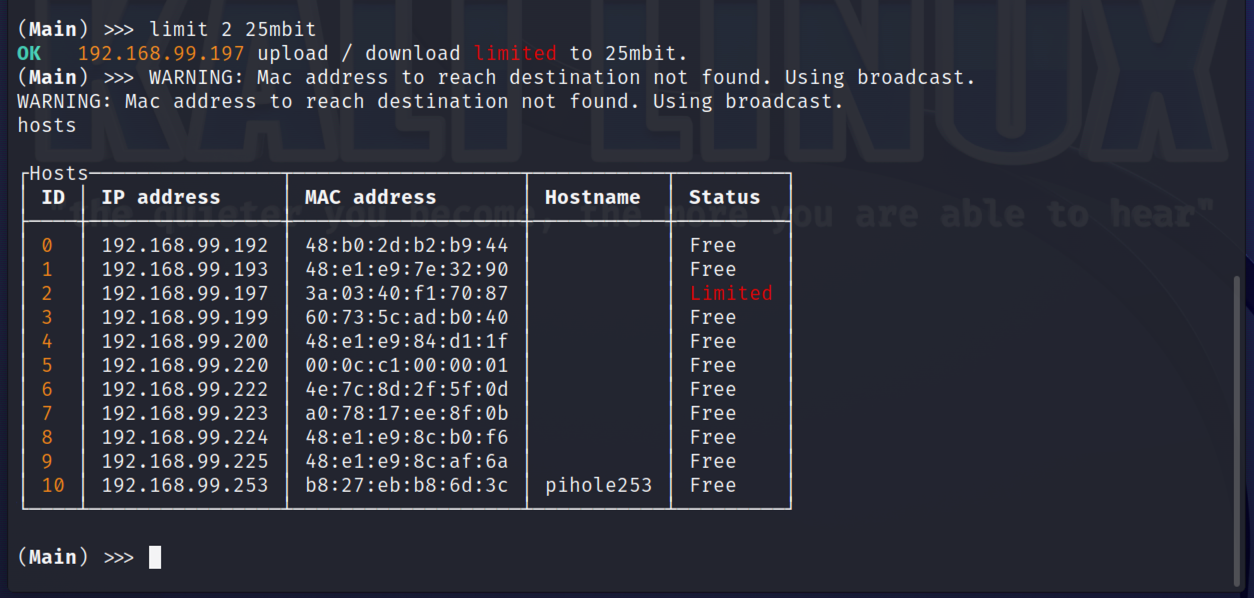
At any prompt you can see which devices have a limit applied by using the hosts command as seen above.
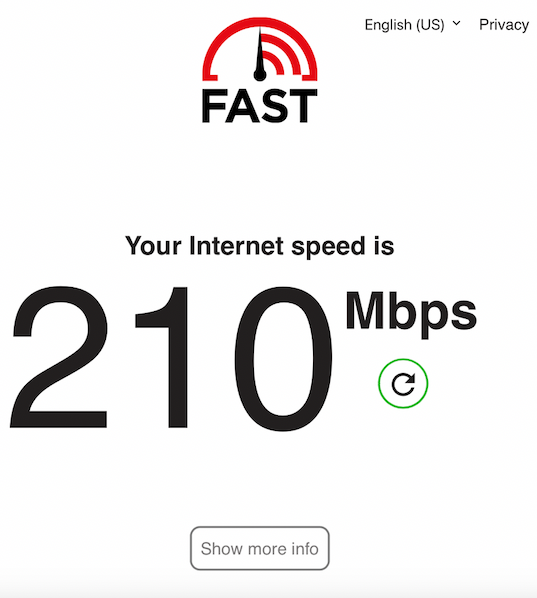
A couple of screenshots from my phone below, show my Internet speed test from fast.com before:
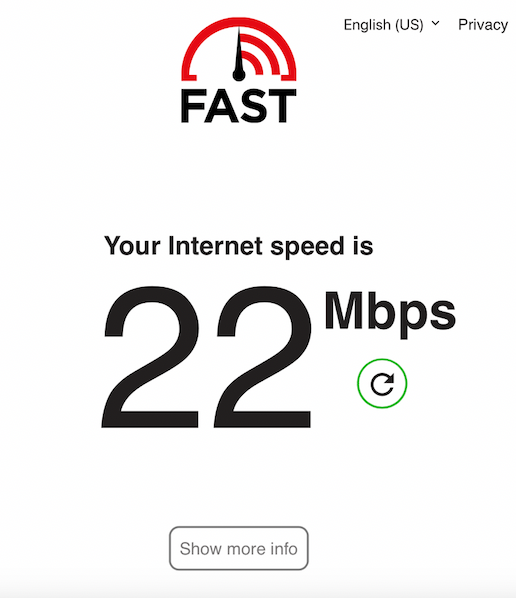
With another screenshot during the limits being applied:
Below I clear the limit applied to my phone, before then blocking it entirely.
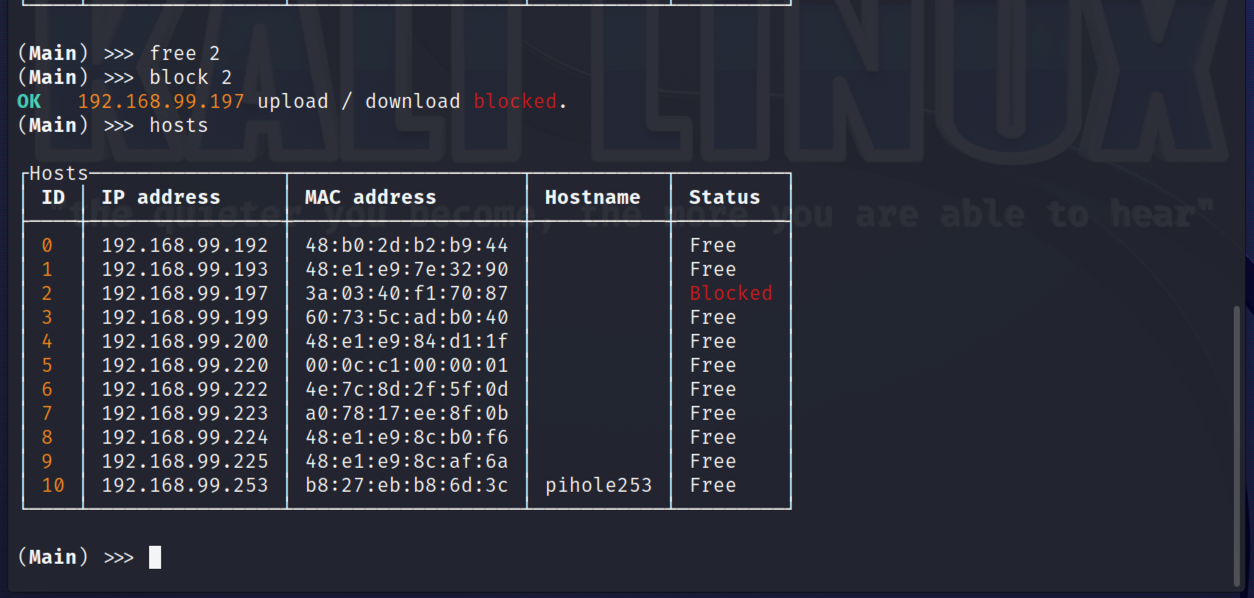
After confirming my phone now appeared to have no access to the internet via the Wi-Fi connection, and rather annoying it didn't flip over to mobile data. Its time to unblock my phone using the "free all" command.
Finally I exit the Evil Limiter application, after being more than a little impressed with the tool.
